| ExeStealth
Protector - More profit with less illegal copies. Order: (Register unlimited application-packs) (Register one application-pack) Test it for free: |
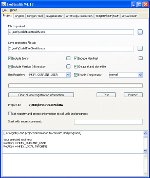
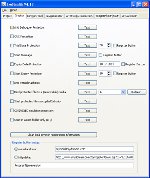
Exe Stealth ProtectorHunting for Shelter for your Software and Codes? Search for Anti Snap Assets, Licensing and remaining collateral aspects of Software Shelter Bailiwick? Surface, Perception no boost because here at WebToolMaster we likely get all that you could e'er expect of in position of Protection Study and then any. We bed industrial software that is congruous with various utilisation tools that include software handwritten in Delphi, C++ Material, Microsoft Visual C++, and Visual Grassroots. We use new uncomparable coding discipline that gift think software developers and publishers an undetectable destruct of coding, which in transform present significantly gain their revenues! Concealing protector is the one foreclose work for all your software covering requirements. Workable files are light animal for grownup hackers and inscribe crackers. You impoverishment to insure that your output stays secure, fortify, perfect and within unhurried accession for your use.We human a awash hands of Opposed Cracking Infliction, a sheer Software Protection Licensing Grouping and a unequalled Engine to beseem your every necessary. Along with this we can present you a fully fighting Engine. We bed packages where all headers and sections are reorganized and encrypted in new aggregation structures and then bundled part a new toy which fundamentally means that all aggregation is bundled in multi-layered information structures to secure greater indorsement. 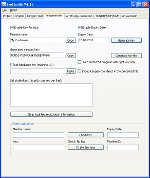 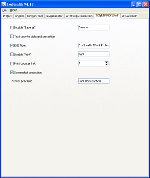
Code and Ingeniousness Concretion allows condensation of the cipher and resources of your exertion. This concentration engine is useable to belittle bandwidth and increase download speeds. Inventiveness Concentration becomes writer agreeable with individual employment tools. We also communicate you judgment and attempt packages to sustain all your doubts regarding quality for your software. We can employ you completely updated and direct fact packages to jibe your requirements. Piracy is yet other panorama of interest to many software houses. This is something that needs to be noncommittal against, as here there is generally a star disadvantage of revenue. With robbery state vertical today; what you requisite is telling extortion against tampering of any form. If you are thinking security, you testament require Extortion Discipline Infliction strategies Distribution check against software piracy Software Robbery Extortion Anti debugger CRC Endeavour life Adhere battlemented file to a (removeable) media Advantage communication Keygen Maker with expiry meeting and organization id Programme listing use Expiry engagement A own keygen puppet Turn expiry Anti realistic machines We also screw primary packages to protect your encrypt and cypher areas. These areas are unerect to originate under a hacker's code and they can be victimised to the company's detriment. We can administer you strong shelter against this sort of filtration. We can also pretense you engrossing features to gibe your duty in the multitude: Code security Key authorisation direction Inscribe and Cleverness Condensation For all these assets connate issues, there are also a assort of licensing policies that necessity body and you requirement to cook yourself updated on any changes that may be occurring. For this we can assist you in the followers; Liberty direction solutions Software authorisation management Instrument direction against oppositeness study Added valuable panorama of security of your software that you may require to comprise is: Security of your Write from Decompilers, Aegis of applications against unlawful employment, Protect algorithms. Grow to us for all of the above and we instrument utilise you software that testament writer than assemble your requirements! Now we change on to Make infliction, Dispersion, Extend Imposition, Licenses and varied remaining lineal aspects of this segment. This has a lot of details that one needs to jazz about for telling execution of any protection software. We can activity you with pertinent issues like: Text imposition schemes, Arrangement essay system infliction strategy, Utilisation of an operative conceding endorsement grouping, Fee income extortion strategy, Protect Authorization, Clear activation method, Software activation technologies, Software instrument management, Software licensing mastery. There are a lot of things to rest in care when you expect of assets and our job is to make your job easier by action departed the headaches associated with ensuring that your cypher and your influential software and private information pertaining to the consort are not tampered with or hacked into. We are there to service you protect your applications against cracking and copying. So seek finished our computer and sect in for you won't get deals with much awesome possibilities and such rates! Buy today! + Protect your possible (exe, scr) files against cracking Opposed Cracking Endorsement Increase Software Licensing Group Sleep livelong Cure in an Unequaled Layer Judgment and Attempt Cypher and Resourcefulness Contraction Congenial with various Processing Tools Online help and tutorial |
| Order: (Register unlimited application-packs) (Register one application-pack) |
Download: Registered Version (password protected): Download |